Microsoft advises users to disable the Windows print spooler or risk being hacked.
Microsoft advises users to disable the Windows print spooler or risk being hacked.
This is the third major Windows
print flaw discovered in the last five weeks.
Facepalm: Microsoft is once again
advising customers to disable Windows print spooler, following the discovery of
a new vulnerability that allows hackers to execute malicious code on machines.
While a patch to address the flaw will be released soon, the most effective
workaround for the time being is to stop and disable the print spooler service
entirely.
This is the third flaw in the
print spooler discovered in the last five weeks. While a critical flaw was
discovered and patched in June, a similar flaw known as PrintNightmare was
discovered shortly after and patched as well (with mixed success).
The discovery of this new
vulnerability is discouraging news for Microsoft and its customers.
Microsoft has issued an online
warning to customers about the new print spooler vulnerability, writing,
"An elevation of privilege vulnerability exists when the Windows Print
Spooler service improperly performs privileged file operations." An
attacker could then install programs, change or delete data, or create new
accounts with full user privileges."
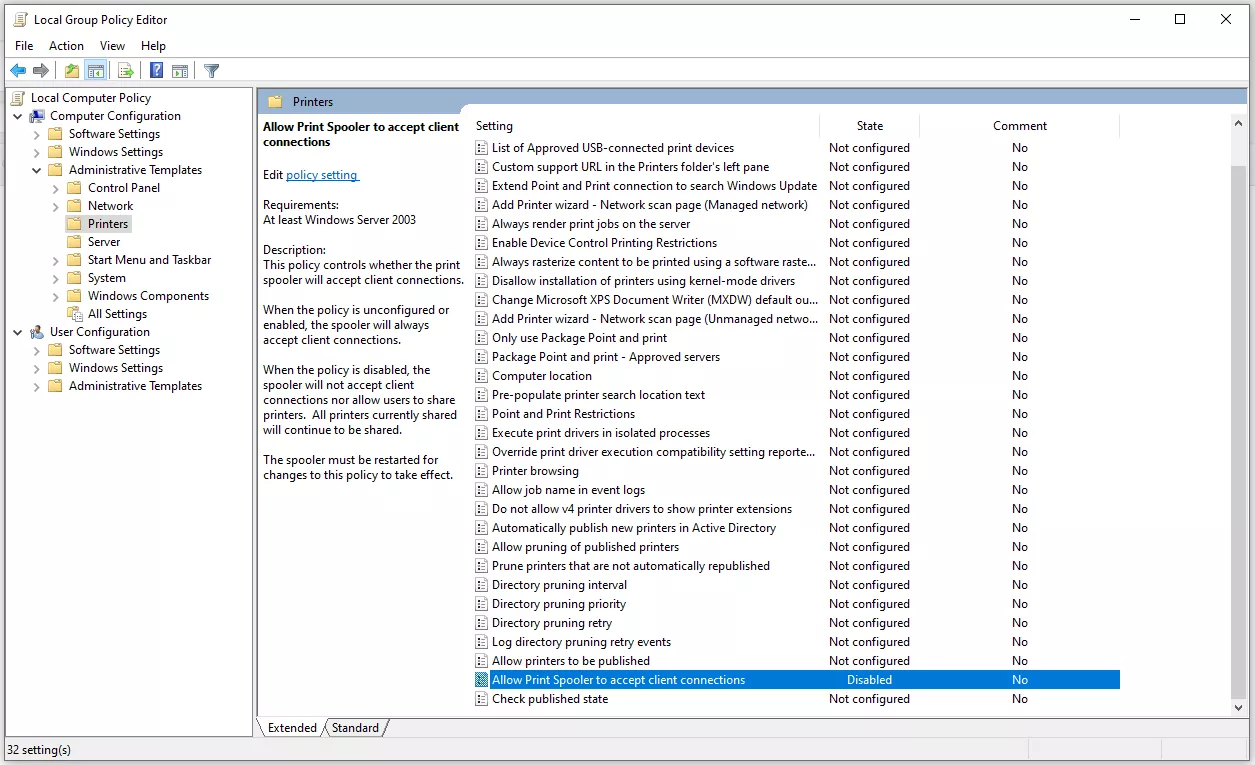
This is extremely important!
If the "Print Spooler"
service is enabled (which is the default), any remote authenticated user can
execute code on the domain controller as SYSTEM.
Now is the time to stop and
disable the service on any DC!
The bottom line for keeping your
computer safe is to stop and disable the print spooler service if it's running
– Microsoft explains how to do so online. While a patch for this vulnerability
will be released in due course, no timetable is currently available.




Comments
Post a Comment